Top Notch Info About How To Protect From Conficker

To verify that the standalone cleaner.
How to protect from conficker. A list of the free conficker removal programs is available on the web site of the conficker working group, an alliance of companies fighting the worm. Our antivirus protection can stop downloads of malicious files and complements the antivirus protection available at endpoints. Ad scan malware, phishing, & ransomware threats on your apps, users, data, devices, & emails.
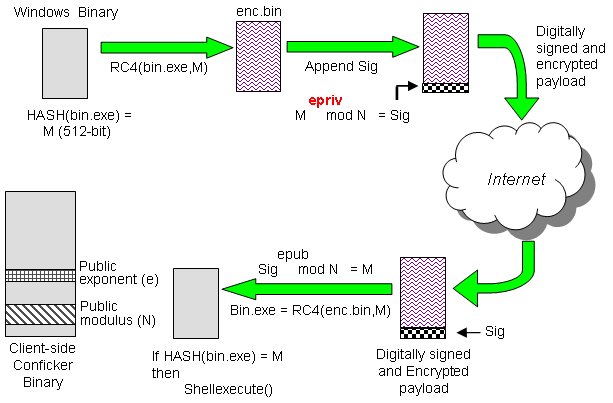
Do more than just have antivirus scanners, use the best free cybersecurity detection too. Its version b, c, d, and e. Conficker is a work of malware that, in the form of multiple variants, has been worming its way through unpatched windows desktop and.
Do more than just have antivirus scanners, use the best free cybersecurity detection too. Download and install the latest version of your eset software. Learn more & get started today.
Ad scan malware, phishing, & ransomware threats on your apps, users, data, devices, & emails. The most recent microsoft security intelligence reports (sir) describes the ongoing threat of the conficker worm and urges businesses and individuals to apply security. Update your virus signature database.
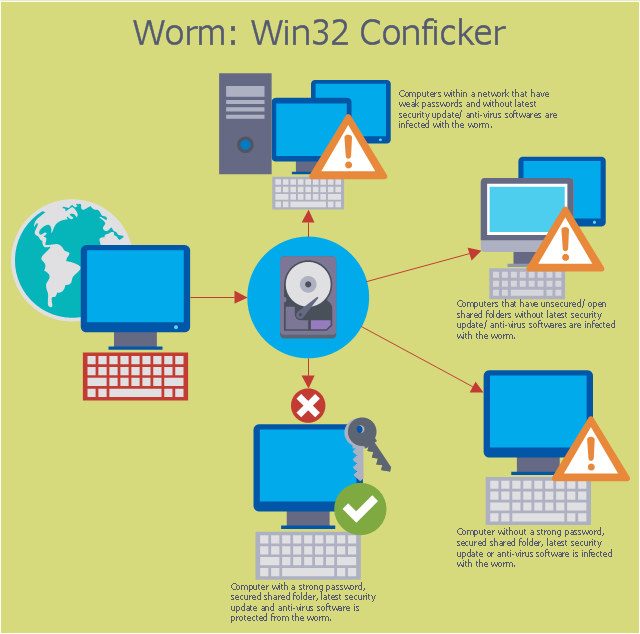
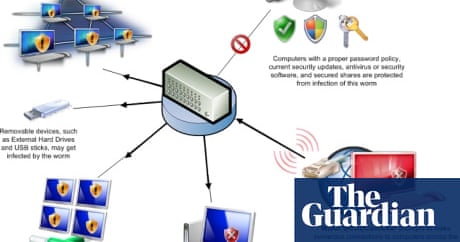
To protect itself from removal, conficker disables the security systems of a computer it infects. The only solution that blocks every threat from every path in your network. Ad detect and block cyber threats before they reach your security stack.
Read how you can protect your pc here. The conficker worm (also known as downup, downadup and kido) is probably the most prevalent computer worm on janet and the internet at this time. Ad powerful device and software protection.